Tag cybersecurity
Four Ways to Prepare for a Data Breach in 2022

Why Do Cyberattacks and Data Breaches Happen, Anyway?

Intel Processor Security Issue – What You Need To Know

3 Things You Must Do to Make Encryption Work for You

The Password Switch: How Safe is Your Cyberspace with Two-Factor Authentication?

EFI Firmware: Not So Firm? Gillware’s Take on Apple’s Firmware Issues

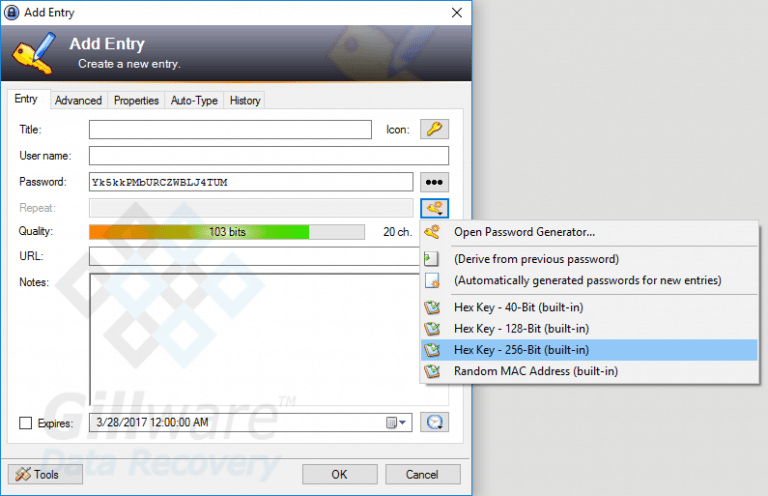
Making Strong Passwords to Protect Your Data